AML Transaction Monitoring Explained: How to Catch a Money Launderer
Businesses have a real challenge when it comes to anti-money laundering (AML). Criminals are constantly innovating how they hide their funds, and new technologies are making it faster and easier to move money around the globe. Banks need to stop these bad actors while complying with the laws and regulations around it.
Of course, money launderers aren’t making it any easier—they launder as much as 5% of the global GDP in a year. So, how do businesses aim to catch this approximately $2 trillion of money laundered? By deploying the best AML transaction monitoring software they can.
That AML and transaction monitoring solution can have a custom construction. But some of the available tools make a bigger dent in money laundering than others. In this article, I’ll dive into AML monitoring and how it works. Then I’ll share the best methods institutions can use to monitor transactions.
What is an AML transaction monitoring program?
AML transaction monitoring is the process of monitoring financial transactions to identify activity possibly related to money laundering or terrorist financing, then flagging it via a suspicious activity report (SAR). AML monitoring is required by various laws in the US, Europe, UK, and elsewhere.
In the US, the Bank Secrecy Act requires financial institutions to have an AML program. That program must be able to reliably detect and report suspicious activity.
In any case, AML monitoring must be able to:
- Report money laundering and terrorist financing
- Comply with regulations
- Conduct the most crucial piece of AML—transaction monitoring
Transaction monitoring in AML software detects transaction patterns for possible money laundering or other financial crimes. It involves data collection, risk assessment, rule-based scenarios, alert generation, and case management. In modern software, machine learning and AI greatly enhance the capabilities of each.
Data collection and risk assessment
AML data collection comes from various sources, including transaction data, customer data, and watchlists. Once compiled into a database, an institution can analyze and comb for suspicious behavior.
One way to analyze that data is through risk assessment. AML transaction monitoring software assesses the risk associated with each transaction and customer. “It bases that analysis on factors such as transaction history, customer demographics, and geographic location. It can even compare that customer’s activity to other similar customers to see if something is out of character. Then, high-risk transactions and customers are flagged for further review.
Rules-based scenarios and case management
Rule-based scenarios work as part of risk assessment. AML transaction monitoring software identifies potentially suspicious activities based on pre-defined rules. These “scenarios” specify transaction patterns or activities matching previous financial crimes. For example, a rule may specify any transaction above a certain threshold must be reviewed for suspicious activity.
When the system flags a transaction or activity as potentially suspicious, it also generates an alert. Then an analyst investigates the transactions in question to determine if they are indeed suspicious.
Investigators organize their documentation on these manual reviews using case management tools. As part of case management, they also collaborate with other investigators and generate reports for regulators and law enforcement agencies.
Machine learning and artificial intelligence
Machine learning puts the power of computing to work running data collection, risk assessment, and case management. These systems can learn from previous transactions and adjust their detection algorithms accordingly. They often detect patterns that are significantly harder for human analysts to spot. One trend of AML transaction monitoring solutions is to add real-time capability. This allows the monitoring of transactions in real-time payment apps like Zelle, Venmo, and CashApp. Some transaction monitoring systems, like DataVisor’s, are fast enough to detect irregular transactions in milliseconds.

What does AML transaction monitoring detect?
AML monitoring doesn’t just detect money laundering. It detects suspicious financial activity that could be terrorist financing or other financial crimes. Among all types of suspicious activities, a few specific indicators stand out as risky.
Unusual transactions
AML monitoring flags abnormal frequency, volume, or patterns of transactions as potentially suspicious. A series of transactions just below the reporting threshold would be flagged. So would a large transaction that is out of line with a customer’s typical transaction history. Then, it’s up to the investigator to look into things further.
Structuring
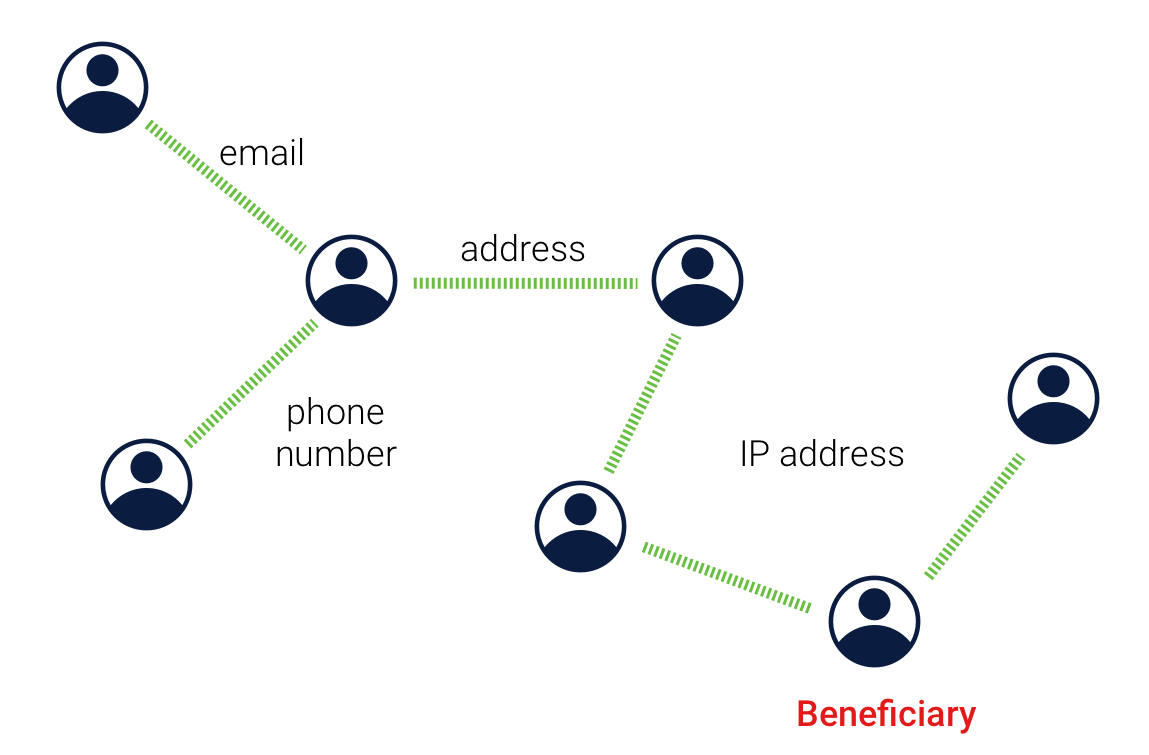
Criminals attempt to avoid detection by breaking up transactions into smaller amounts. AML transaction monitoring software can identify these patterns of structuring activity and link the unusual transaction together.
Source of funds
If a customer suddenly deposits a large amount of cash into their account, AML software will catch it. Analysts then investigate the source of the funds to ensure that they are not proceeds of crime.
What can go wrong with AML transaction monitoring?
Depending on the solution you’re using, AML transaction monitoring software can hit one or a handful of issues. Some require better internal processes. Some require better software altogether.
Common AML monitoring problems
False positives
Any case of potential money laundering that doesn’t actually warrant a manual review, but is flagged anyway, is a false positive. These are among the biggest problems in AML monitoring and harm customer experience. It is not uncommon for false positives to account for 75% or more of total volume.
Seemingly suspicious but still legitimate activity can trigger false positives. For example, someone sending another family member $25,000 as a gift when they normally wouldn’t send more than $100. Incomplete or inaccurate data is another potential cause—like missing customer information. An AML monitoring system that relies too heavily on rules-based decisioning is also a common issue. An AI-powered approach can uncover hidden connections between transactions and capture unknown financial crimes. These systems also triage alerts and prioritize them, making bulk actions easier for investigators.
Ineffective detection routines
Ineffective detection means having gaps in your AML coverage. These ineffective routines can have several causes, like:
- Over-reliance on rule-based systems
- Lack of system integration
- Lack of staff
- Over-reliance on manual reviews
Ineffective detection routines tend to be an internal process problem. But those internal processes are often improved by implementing a better platform.
Too many rules/scenarios
Giving your rules-based system too much to track sets it up for failure. More scenarios increase the possibility of duplication errors and wasted investigation time.
Keeping scenarios manageable comes down to the right internal process. Review your AML solution and your current transaction monitoring based on the needs of your business first. Be sure to consider customer experience as well. Prepare for the scenarios you know you will face and ensure you have the right AML monitoring in place to handle them.
Inability to use internal data
Poor internal data usage sets your AML monitoring up to hit increased false positives. It also reduces efficiency and accuracy.
More than that, it puts you at risk of non-compliance—and potentially on the hook for severe compliance penalties.
Improved internal processes are key to funneling internal data to your AML monitoring platform. Team communication is key, right alongside knowing what your solution is capable of.
Failure to incorporate new products
New AML monitoring technologies improve many crucial areas of transaction monitoring. They use resources better to improve detection accuracy and speed. Most come equipped to tackle new challenges like virtual currencies and real-time payments.
On the flip side of the coin, failure to incorporate them results in a worse-performing AML monitoring system. It also increases risk of non-compliance as money laundering slips through the cracks.
Incorporating new AML monitoring products falls to internal leaders to make a decision. No matter how you build an AML monitoring solution, adding new technologies to it means looking at the best-in-class options and what they do.
AML transaction monitoring software with AI
Standard AML transaction monitoring solutions feature the capabilities we explored earlier. But they are also customizable to the needs of the financial institution.
Many of the capabilities that AML transaction monitoring solutions offer today rely on AI and machine learning. For years, AML transaction monitoring meant using rule-based scenarios to flag transactions for review based on past attacks. Methods like rule-based scenarios and expert reviews still have their place. Yet their effectiveness improves when supplemented with machine learning tools. With AI, institutions can detect and respond to suspicious activities in real time. AI can even automate things like risk scoring, watchlist screening, and case management. A well-trained algorithm can replace the cost of manual reviews while increasing detection accuracy.
DataVisor’s own well-trained algorithm offers market-leading detection speed for AML monitoring. It consolidates alerts for one case review and reduces false positives, saving time and improving efficiency as much as 10x. Explore how it keeps teams laser-focused on detecting money laundering by talking with our team to see the platform in action.
Latest Articles